Advisory: iOS 14 and Android 10 – How do randomized MAC addresses affect your network? [UPDATED]
Last Updated: 15 Oct 2020
Publication Date: 24 Sep 2020
What is Randomized MAC and what is it for?
With the recent launch of IOS 14 and Android 10, a new feature is introduced which configures the phone to use a randomized MAC address when connecting to a WiFi network.
The feature is enabled by default to prevent the phone from being tracked across different WiFi networks, thus improving privacy for the user. It is known as Private Address for IOS 14 and Privacy for Android 10.
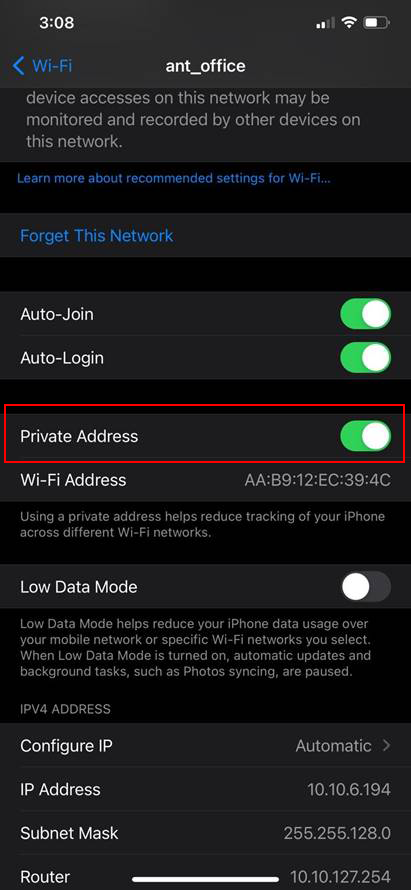
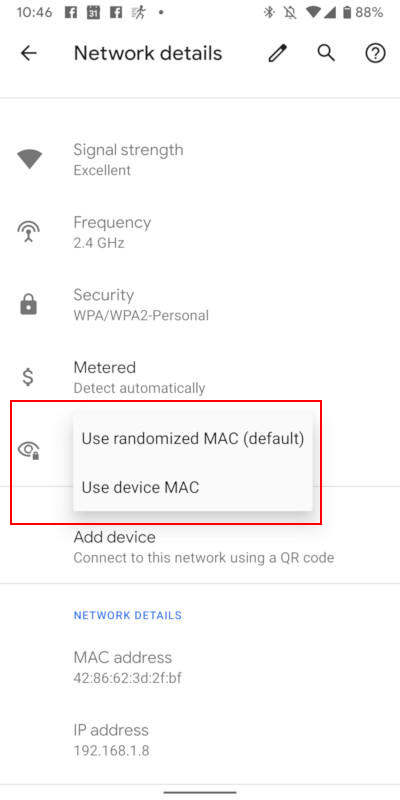
Does IOS 14 use a random MAC address every 24 hours?
No. IOS 14 will not create a random MAC address every 24 hours.
This feature was originally included in the early beta releases and was removed from the final release. Articles that are circulating on the Internet describing this behavior is all based on information from the beta releases.
How does it affect you as the WiFi Managed Service provider (MSP)?
The same random MAC is always assigned for the same SSID / network, therefore, there is no impact to relogin to the same network.
However, if you operate different SSIDs in the same venue, your users will need to login again when they move from one SSID to another.
Also, if you have specific network access rules that are based on MAC address, you will either need to update your rules based on the phone’s randomized MAC or you will need to advise the end-user to turn off the Randomized MAC feature in order for the correct network policies to be applied.
Is there any impact to your existing users?
They will then be prompted to login to your network again.
For existing users that are already login to your network, if they upgrade their Android version to 10 or IOS version to 14, the MAC address of these users will be changed and our gateway will no longer recognize them as login users.
Can the MSP do anything to automatically turn off or work around this feature?
Unfortunately, there is no automatic way to disable this feature.
This feature was released by phone manufacturers as a tool to enhance privacy by giving more control to the end-user. Therefore, unless the end-user willingly chooses to disable this new privacy feature, the MSP cannot get the device’s original MAC address.
Another approach to mitigate this impact is to deploy Hotspot 2.0 solutions.
Talk to us to know more about ANTlabs Hotspot 2.0 solutions.
Sources:
iOS14 Release Notes
WiFi – The payload for configuring Wi-Fi on the device
Android 10 Release Notes
iOS 14 MAC randomization privacy feature may cause Cisco enterprise network issues
